 Blog
Blog
How RansomHub Breached Over 200 USA Businesses in Just Several Months
How do these cyberattacks keep occurring? It’s an honest question that any business has a right to ask. We hear of new advanced security tools being released regularly from some of the world’s top security vendors, and yet cyberattacks continue to capture headlines. Reasons for Perpetual Cyberattacks The persistent threat landscape of today stems from…

-

How Comprehensive Logging Can Stop the Next Big Cyberattack
Imagine logging into your organization’s system one morning only to discover threat actors had exfiltrated all of your current and past customers’ data. Or picture trying to log on and realizing hackers have locked you out of your systems. Although these two situations are hypothetical, the story is all too familiar. In the last few…
-

The Fatal Flaws of Poor TDIR in Ransomware Recovery
Imagine a coastal town bracing for an impending hurricane. As the storm approaches, the community mobilizes in a flurry of activity. Residents come together to board up windows, place sandbags, and secure loose items. Local and national media descend upon the area, their cameras capturing the frantic preparations, the storm’s fury, and the initial aftermath. …
-
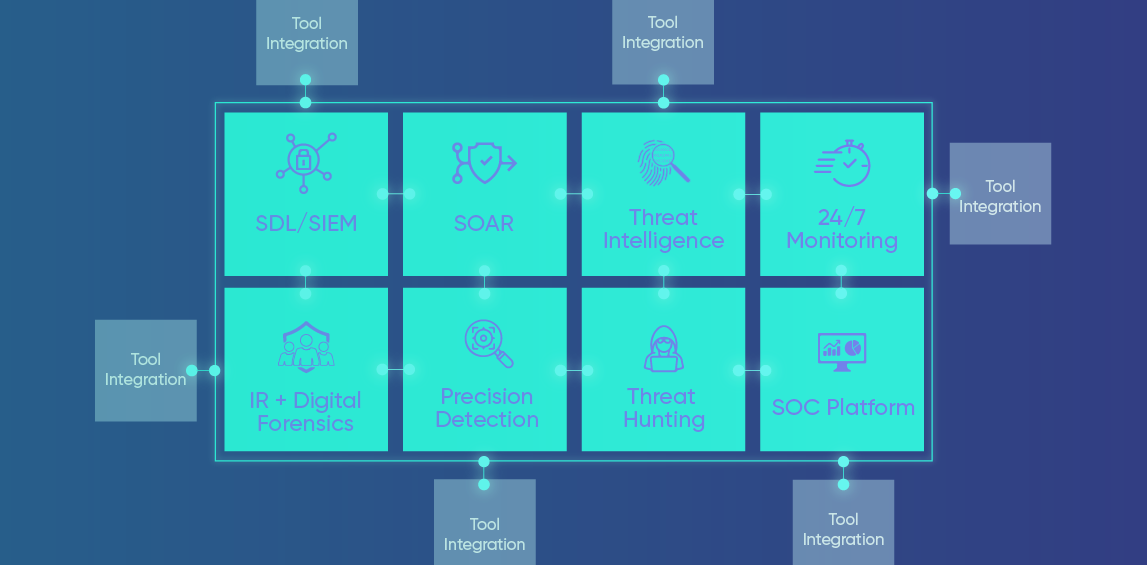
The Evolution of SecOps: The Essential Components of MDR
As threat actors launch more sophisticated and AI-enhanced attacks, traditional preventative measures alone are falling short. Adequately protecting an intricate web of modern infrastructure — a blend of on-premise and cloud-based systems, numerous mobile devices, and many applications — while navigating increasingly stringent compliance regulations demands a more proactive and holistic approach. Plenty of cybersecurity…
-

Should Your Security Solution Be Agent-Based or Agentless?
Agent-based or Agentless Security? This has been a longstanding debate among IT professionals. It is a hot topic that has gained more prominence in the cybersecurity community following the well-publicized CrowdStrike incident that disrupted computers globally. But what exactly is an agent, and how can security be managed without one? Before delving into the specifics…
-

MDR Clarity – Cutting Through Common Misconceptions
The cybersecurity solutions industry is a complex maze, filled with acronyms and overlapping services. New solutions emerge at a dizzying pace and, in some cases, rebranded versions of existing offerings to align with the latest trends. Security leaders and decision-makers are left swimming in a bowl of alphabet soup as they try to understand the…
-

The Security Data Lake Revolution – Ditching SIEM for Advanced Threat Detection
The relentless march of technological evolution ensures that today’s cutting-edge innovations will inevitably give way to tomorrow’s superior alternatives. While these old technologies continue to be used by some, almost everyone eventually moves on. DVD players, once ubiquitous, have been largely replaced by streaming services, yet some still maintain personal libraries. While some older generations…