Don’t Get Hooked by a Phishing Scam

After a brief decline in 2019, phishing attacks spiked again in 2020. Last year, they were so prevalent that one in every 4,200 emails was a phishing scam. Businesses lost approximately $17,700 every minute due to a phishing attack. Research from the FBI’s Internet Crime Complaint Center found that phishing (including vishing, SMiShing, and pharming) was one of the biggest cyber threats, with nearly a quarter of a million people reporting that they fell for a scam hook, line, and sinker.
Attackers Went Phishing, CYREBRO Cut the Line
In January, one of our clients received a phishing email from what appeared to be Microsoft but contained a link that ultimately led the user to a phishing site. The eagle-eyed employee who received the email noticed that something about it felt ‘off.’ Instead of following the instructions in the email, he forwarded it to us to investigate it further.
Our Digital Forensics and Incident Response team jumped into action and examined the email. They quickly confirmed the employee’s suspicions: the email was not coming from Microsoft and the link, which appeared to come from a prominent non-profit, did not direct the user to that charity’s site. The CYREBRO team investigated the email and found that the initial link in the email redirected several time. The attackers utilized an Open Redirect vulnerability in one the non-profit’s pages. This shows that the attackers were able to exploit a vulnerability in the non-profit’s site, allowing them to redirect the user to their phishing page through the non-profit’s link. The final redirection was to a simple fake Microsoft login page asking for the user’s credentials. Had the user entered his details, the credentials would have been sent via POST to the phishing domain.
Here’s a look at this particular phishing email:
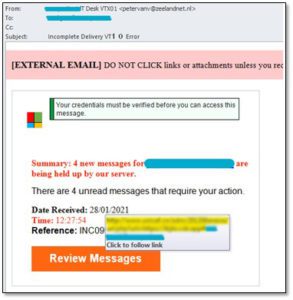
The attackers tried to take advantage of the fact that Microsoft is a trusted company and one used by the client, but there are several red flags:
- The Microsoft logo doesn’t look like the brand’s actual logo, nor does the font.
- Microsoft is a highly reputable company; reputable companies never ask users to verify their credentials in this manner.
- Microsoft never sends users emails that claim messages are ‘being held up by our server.’
- When hovering over the link in the email, it reveals a suspicious-looking URL
The indicators of the attack were added to CYREBRO’s threat intelligence platform, which is available to all our clients, so no others would be targeted or become potential victims of this phishing scam.
The Dangers of Being Baited by Phishing Emails
Had the email recipient not been so diligent, the hackers could have reeled in a huge haul. We have seen in past phishing attacks that if the user clicked and logged into this type of fake Microsoft page and then entered their password, within 6-48 hours, the attackers log into the user’s mailbox. From there, hackers can access and steal information. But landing one small fish is often not enough for bad actors.
To make the most of their attack, they start impersonating the user through their email account, performing fraudulent activities, and defrauding others in the company. The big score comes when the attackers start communicating with the finance department, requesting sensitive banking info, changing account information, or rerouting payments to their own accounts.
Best Ways to Identify a Phishing Email
Now is the time to be vigilant and make sure every person in your company behaves that way; your business depends on that. Attackers often use the same types of manipulations over and over to defraud email recipients.
Impersonating a legitimate company: Attackers leverage the trust we have in the biggest brands, and the ones we inherently believe are secure – in this case, Microsoft.
Miswritten URLS: With typo squatting, hackers will either change a single letter in the URL or add an incorrect top-level domain. For example, Microsoft is always Microsoft.com and would never be written as Microsoft.co or Mlcrosoft (written with a lower case ‘l’ instead of the correct ‘i’.
Improper-looking logos: Bad actors will recreate the ‘sender’s’ logo but usually do a poor job. Most email users who pay attention will notice that the logo is wrong in terms of size, colors, or specific design aspects.
Incorrect fonts: Most corporate companies use particular font families for their branding, whereas hackers use basic web fonts.
Asking for credentials: One of the most common scams involves an email that tells a user their account was compromised and that they need to log in to reset their passwords. As a rule, reputable companies never ask users to enter their credentials via email.
Unusual messages: As in the example above, Microsoft never sends users emails that tell them urgent messages are waiting. Hackers use this type of message to tempt users and play into their fears that they are missing essential information.
Don’t Get Reeled In
Business email compromise (BEC) scams cost businesses $1.8 billion in 2020. Scammers are constantly trying to develop more sophisticated social engineering tactics and continue to pray on people’s fears or lack of attention. The internet is a vast ocean with billions of unsuspecting fish who are just going about their business.
As with any business-related security matter, educating employees about potential dangers is the first step. Make sure everyone is aware of how common attacks are and train teams on how to identify inconsistencies. Of course, it’s best never to send sensitive data through email. However, should you be the victim of an attack, ensure that any email which contains sensitive data such as text credentials or unencrypted classified data is deleted from the email account immediately, both from the inbox and from the trash folder. This is something that should be done regularly.
The best rule of thumb is always: if it looks suspicious, don’t click anything. Instead, send it to a security specialist who knows how to deal with it safely and securely. Better yet, employ a threat intelligence system throughout your network to avoid the situation in the first place.


