Two Emerging Vector Trends
Life is never dull for cybersecurity teams, but we’ve seen an increase in two types of threat vectors during the first half of 2021. Reports of the recent Codecov Bash Uploaded security breach is an example of a supply chain attack, while common vulnerabilities and exposures (CVE) have shown up in increased frequency at Apple, VMware, Cisco, and others.
It’s important to understand the nature of these threats, to ensure the security and safety of your network.
Supply Chain Attacks
Computer networks don’t exist in a vacuum. To function efficiently, they need to open pathways to other networks, including those of suppliers and partners. In a supply chain attack, hackers attempt to infiltrate an organization by going after their third-party suppliers and partners. The assumption is that they might have weaker, smaller security networks than the larger target organization, and the hacker will find a point of access indirectly from the supplier. Once they are in the network, they install undetectable malware in the smaller network. Since 2018 there has been a 78% increase in supply chain attacks, according to an Internet Security Threat Report by Symantec.
As networks connect, the piece of malware moves upstream, eventually arriving at the target network. Once inside, the malware can create all types of mayhem, from stealing data to disrupting and bringing down systems.
The Codecov Bash Uploader
Codecov is an online platform that provides hosted testing reports and statistics for its users. On April 1, 2021, Codecov learned that someone had gained unauthorized access to their Bash Uploader script and modified it without permission. The Codecov Bash Uploader supply chain attack bears a number of similarities to the recent SolarWinds attack. In both attacks, the perpetrator used third-party software to gain entry into numerous other organizations, and in both cases, the attack took place in a developer’s environment. The extent of damage caused by the two attacks may never be fully known, and the number of Fortune 500 companies and government agencies impacted was high.
Here is what we know to this point.
The Codecov Bash Uploader is a DevOps tool that had a vulnerability in its Docker image process. In January, hackers gained access to the Bash Uploader script and made unauthorized changes to it.
Those changes included malicious code that stole secret authentication tokens and other sensitive data, which was then sent to a remote site owned by the hackers.
Customer Notifications Beginning on April 30, Codecov began notifying customers that there was a breach. The notification was vague, frustrating customers with a lack of information about the breach, demonstrating a significant lack of accountability, and a slow response in taking responsibility for the mess caused under their watch.
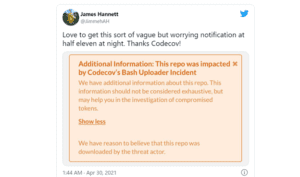
Timeline of the Codecov breach
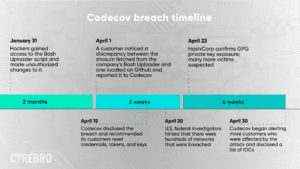
Impact of the Attack
The breach went on for about three months, over which time hackers potentially gained access to thousands of restricted systems. . Small businesses, which oftentimes feel that their limited size makes them invisible to cyberthreats, now find themselves in perhaps greater danger than large enterprises, as many lack the resources to eradicate the threat and ensure that they are no longer sharing their credentials with hackers.
U.S. federal investigators and the companies that were breached are currently investigating the attack. They are reviewing logs and analyzing their networks to see what hackers were able to access.
Codecov Post-exploitation
There have been a few Codecov clients that have performed post-exploitation investigations to learn about the method and steps of the attack, as well as to assess the damage. Both Confluent (www.confluent.io/blog/confluent-update-regarding-codecov-incident/) and Twilio (https://searchsecurity.techtarget.com/news/252500289/Twilio-discloses-breach-caused-by-Codecov-supply-chain-hack) have disclosed their post-exploitation investigations, and the team at CYREBRO has put together a flow of the attack:
- CodeCov is breached
- Data of 29,000 clients becomes exfiltrated.
- The data included keys and tokens to various cloud services. The keys allow access to certain repositories.
- Lack of credential security (including secrets and app keys) allows the attackers to obtain more access
- Lateral movement takes place using these keys with higher privileges
- The attacker gains access to more and more resources, and exfiltrates data
- The attacker gains high privileges that allow them to read and write data, including placing backdoors and persistence
At this point, the attacker has achieved a strong hold on the organization. It is important to understand that the leakage led to the step of further compromise than the initial intention of read-only access to the resource. As can be seen, the lack of security best practices (in handling the environment and credentials of any kind) can result in a catastrophic cyber breach. Later in this article, we discuss steps an organization can take to strengthen its security posture.
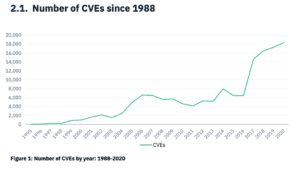
Common Vulnerabilities and Exposures (CVE)
Over the past few months, we’ve observed an increase in CVEs coming from major brands, including Apple, VMware, Microsoft, and Cisco. These include critical, zero-day vulnerabilities that have been exploited and could allow remote code execution on affected systems.
This increase in CVEs has led to an increase in out-of-band patches, as companies need to close vulnerabilities before “patch Tuesday.”
CVEs have been on the rise over the past few years. Redscan’s NIST Security Vulnerability Trends in 2020: An Analysis found that there were “a record number of critical and high severity vulnerabilities were logged to the NIST NVD in 2020, with a notable rise in low complexity CVEs and those which require no interaction to exploit.
Redscan reported that 2020 saw 18,103 vulnerabilities, higher than any other year.
While some of this increase can be attributed to the rise in connected devices, it creates a security nightmare for security teams tasked with securing networks and closing vulnerabilities.
CYREBRO’s Perspective on Codecov, Increase in CVEs
Taking a proactive approach cybersecurity that incorporates a cyber threat intelligence team can better protect client networks against breaches like Codecov, or harmful exposure to IOCs.
“We provide specific recommendations to protect against potential exploitations while embedding our SOC with the ability to identify and mitigate the risk of attack,” said Yael Spindel, Head of the Cyber Threat Intelligence Team at CYREBRO. “We continually enhance our knowledge database, which connects to all our systems. We create new rules based on the data we collect, including IOCs, to catch these attacks before they even begin. This enables us to act proactively and prevent attacks, overseeing and ensuring the safety of our clients’ networks.”
Protecting Your Network
Development environments are complex, and all companies rely on third party software rather than building every application on their own. However, they leave themselves exposed to a Codecov-styled attack.
There are several steps that organizations can take to strengthen their security posture and minimize risk from these types of events.
- Perform code signature checks – Check the software’s digital fingerprint to verify its integrity. Had that been done in the Codecov attack, dwell time could have been limited to hours or days, rather than months.
- Store credentials and secrets in a secure secret’s manager – storing credentials in environmental variables puts your data at risk. Using a secret manager ensures only authenticated users have access
- Upgrade or implement threat detection capabilities – CI/CD pipelines, which was used in the Codecov incident, use automation, which makes it easier for attacks to pass by unnoticed. Upgrading threat detection capabilities could help your team catch anomalies and breaches earlier.
Is your security posture strong enough? Learn more about CYREBRO and see how we can defend your network from attacks.


