Minimal Security Changes That Make A Significant Impact

If you find yourself saying, “I own a small company. I won’t be targeted,” unfortunately, the data is not on your side. Over 40% of data breaches happen to small businesses.
Fundera compiled a list of terrifying facts about cybercriminals, data breaches, and security hacks. It’s enough to make your head spin.
- Cybercrime costs small and medium businesses more than $2.2 million a year.
- There was a 424% increase in new small business cyber breaches last year.
- 54% of small businesses don’t have a plan in place for reacting to cyberattacks.
Now, this is not another doom and gloom article – quite the opposite. With a few tweaks and best practices implemented across your company, you’ll find that minimal changes can have a maximum impact on your cybersecurity.
Let’s break down the simple security measure you can initiate immediately to reduce your risk significantly.
Turn Employees into Security Warriors
The best defense is a good offense, and your employees are the front line.
Raise employee awareness about security issues, explain how to detect a security threat, and make sure they know you rely on them to follow the security protocols you have (or are about to put!) in place. Ensure they know which colleagues are go-to resources for security questions or issues and keep everyone informed of the steps they need to take to remain compliant.
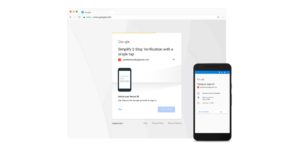
Passwords, Meet 2 Factor Authentication
Case-sensitive letters, numbers, and symbols no longer cut it. Today’s cybercriminals use sophisticated cloud technology to crack passwords, guessing eight-character codes in 12 minutes. Even if you use a password manager, those too can be broken in minutes. The safest option is to require employees to use two-factor authentication, which can prevent 99.9% of hacks.
With two-factor authentication (2FA) or multi-factor authentication, the user is required to verify their identity in two ways. That can be a combination of two of these options:
- Entering a pin or password
- Using a fingerprint or biometric ID
- A device that can receive a one-time code via SMS or an app that can generate the one-time code on demand, such as Google Authenticator
- A hardware-based 2FA device
Usually, a combination of the first and third will be secure enough and simple enough for employees to get used to. Two-factor authentication can be used with almost any cloud-based application, including GSuite, Microsoft Office Suite, Azure, and other cloud storage and services, social media platforms, storage sites like Dropbox, and more.
Sew Up Vulnerabilities with Patch Management
Software development is an imperfect process. Each time a developer or software company releases a new version of the software, a patch update follows within a few days or weeks because a vulnerability was discovered. Cybercriminals will exploit vulnerabilities as soon as they find them.
Enhance your security by applying software patching best practices such as:
- Staying up to date with vendor security updates
- Applying new patches immediately
- Having a patch management policy that defines a schedule to scan all endpoints
- Having a rollback plan in place in case a patch isn’t compatible with your system.
Patch management tools can help you automate these processes or assign them to the IT team.
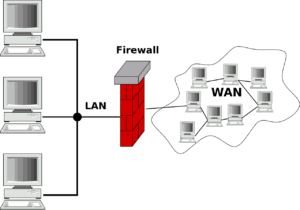
Defend Your Assets with Firewalls & EDR
If your business was a castle, firewalls and endpoint detection and response (EDR) software are like the moat and stone wall surrounding it and making it impenetrable to an attack.
Firewalls create a barrier between your devices or systems and the outside world, preventing unauthorized access. Ensuring employees always have firewalls on before going online will go a long way. The firewall software will alert them if any intrusion is suspected so they can stop what they are doing and let IT know. Add an extra layer of protection for your entire network with a hardware firewall that works through your broadband router.
As the name implies, EDR solutions provide multi-layer protection for endpoints. Instead of taking a reactive approach to cybersecurity, EDR puts companies in a proactive stance. Through a combination of real-time monitoring and analytics, EDR tools use automation to detect and mitigate threats, preventing attacks before they enter your system.
Wrap-Up
As a business owner, you innately have a smaller security budget than an enterprise, which makes you a prime target for cybercriminals. Keep in mind that maintaining a high level of security is not a one-and-done type situation. As technology continues to evolve, so do cyberattacks. However, by initiating the minimal, free or low-cost solutions we’ve mentioned and adapting enterprise-like cybersecurity measures to your business, you’ll make significant headway towards fortifying your company’s security and preventing your company from becoming a statistic.

