The New Phishing Method That Bypasses MFA

Security experts, including our team at CYREBRO, tout the benefits of using multi-factor authentication (MFA) for an added layer of security. While that is still sound advice, recent research shows that a new phishing technique, which steals authentication cookies through Microsoft Edge WebView2 applications, can render MFA useless if people don’t take other precautions.
Discovering a new attack method
Threat actors’ attack patterns constantly evolve as they look for new ways to wreak havoc on unsuspecting users and cash in on bad behavior. In this ongoing game of cat and mouse, hackers begin launching new attack vectors, security experts identify them, and vulnerabilities are addressed. Then the game starts over.
The wide adoption of MFA stems from exactly that pattern. Bad actors routinely stole user credentials and used them for malicious activity or published them for others to use. When companies started using MFA, unless hackers could also access the required one-time MFA security code, the stolen user information was no longer enough to access applications, systems, and networks.
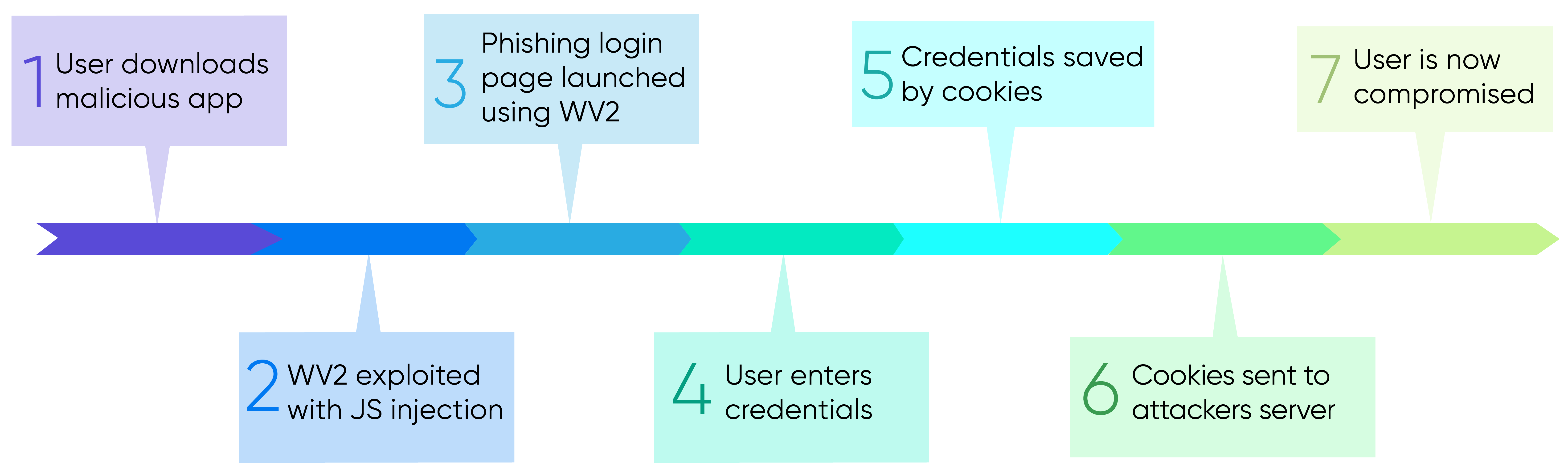
Although it seemed like the cat finally caught the mouse and MFA was a solid security strategy, a cybersecurity researcher who goes by the online name mr.d0x has pioneered a new type of phishing method. The attack, dubbed WebView2-Cookie-Stealer, allowed him to steal authentication cookies and log into accounts, completely bypassing the MFA requirement. His attack point was Microsoft Edge WebView2 applications.
What are Microsoft Edge WebView2 applications?
According to Microsoft, “The Microsoft Edge WebView2 control allows you to embed web technologies (HTML, CSS, and JavaScript) in your native apps.” Developers can use the technology to create an executable that communicates with web apps like a browser, giving desktop apps more capabilities for interacting with web apps.
A look at the WebView2-Cookie-Stealer
WebView2 offers developers plenty of advantages but enables them to access cookies and inject JavaScript into application-loaded web pages. Attackers can use malicious JavaScript like a keylogger, stealing and sending authentication cookies to their remote server.
In mr.d0x’s sample attack, the executable uses the embedded WebView2 control to open an authentic Microsoft login form, capture keystrokes, and extract the cookies after authentication. From there, hackers can decode the base64 format to reveal the cookies.
mr.d0x also showed that Chrome cookies could be stolen and exported by using WebView2 to launch with a pre-existing User Data Folder that includes bookmarks, passwords, and session data. Threat actors can then extract the cookies to their servers. All that’s left for the attacker to do is open the user’s login form, import the cookies with a Chrome extension, and refresh the page, at which point they will be authenticated.
Since the cookies are taken after the person has logged in and used MFA, the attacker doesn’t need the MFA code or key. The additional danger is that the cookies are valid until the session expires or someone detects the attack with a post-authentication check – a rare practice for most companies.
How can you avoid becoming a victim?
At the end of the day, the WebView2-Cookie-Stealer is simply a social engineering attack, so companies should follow the same cybersecurity practices they would to defend against any phishing attack.
In an interview, Microsoft told BleepingComputer, “We recommend users practice safe computing habits, avoid running or installing applications from unknown or untrusted sources, and keep Microsoft Defender (or other anti-malware software) running and up-to-date.”
CYREBRO’s Threat Intelligence Analyst Ziv Nachman says:
“WebView2 has closed the gap that reverse proxy couldn’t – authentic and seamless MFA bypass. Since this method is only research and hasn’t been abused in the wild yet, awareness and staying alert are critical. Some good practices are avoiding downloading apps when a web service is available and not using apps you are unfamiliar with. Most importantly, always second-guess whether it makes sense for a system to request your credentials at a certain stage when a login form is opened.”
It’s always safer to download apps directly from a site (i.e., only download Abode apps from the Adobe website), and avoid downloading apps from unverified sites, like when North Korean hackers mass distributed old versions of VLC containing a vulnerability for later exploitation.”
Given that 98% of cyberattacks involve some form of social engineering and the average organization is targeted by over 700 social engineering attacks yearly, every employee needs to remain vigilant.
Cyber awareness is one of the most powerful protective strategies in any company’s defensive arsenal. While mechanisms like MFA that once seemed 100% secure will rise and fall, cyber awareness goes a long way in helping you avoid the cat and mouse game from the get-go.